Categories: Featured Articles » Home automation
Number of views: 7622
Comments on the article: 1
Internet of things - what is it?
The Internet of Things (IoT) is a wide network of objects connected via the Internet and capable of exchanging data. This is not only a lot of different devices and sensors, interconnected by wired and wireless communication channels and connected to the Internet, but the tight integration of the real and virtual worlds, in the environment of which communication is carried out between people and devices.
Concept and background for the birth of the “Internet of things”
Due to the widespread use of smartphones and tablets, by 2010 the number of devices connected to the Internet increased to 12.5 billion, and this with a world population of 6.8 billion, that is, almost 2 connected people per inhabitant of the earth already in 2010 to the device’s global network.
These devices are capable of connecting to the network and interacting with each other via Bluetooth, Zigbee, WiFi networks, via cellular networks, via satellite network, etc. Analysts do not exclude that by 2020 the number of such devices around the world will reach 50 billion. In connection with this state of affairs, it is not at all surprising that such a phenomenon as Internet of Things or Internet of the Things, abbreviated IoT.

The concept of the Internet of things consists in the emergence of a computer network of things, a network of physical objects with integrated technologies of interaction both among themselves and with the external information environment and simply with the external environment of the real world.
The presence of such a global network of things is capable of fundamentally restructuring not only social, but also largely economic processes. And a person, of course, will be excluded from the main part of all independent operations and actions of things, his participation for the current work of the system will no longer be required.
This idea was formulated back in 1999, when the prospect of expansion became apparent. radio frequency identification means more and more on objects, on their interaction between themselves and with the world around them. Since 2010, the trend has clearly formed, and the information technology of wireless networks, cloud computing, machine-to-machine interaction, an active transition to IPv6, software-configured networks - began to fill the concept with real opportunities.
Features of the “Internet of Things”
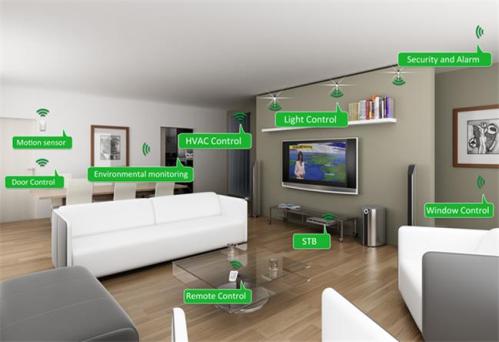
What is the result. For domestic use, the effect is colossal - home automation, not a new phenomenon at all, is expanding by combining things into a computer network, that is, through the use of Internet protocols, the phenomenon of fully automatic process execution is achieved.
An alarm clock and air conditioning, a lighting system and a garden watering system, a security system, light sensors and heat sensors, even medicines equipped with an RFID tag, now all interact with each other via infrared, wireless, power and low-current networks. The coffee maker turns on, the illumination changes, a reminder about taking vital tablets is triggered, the temperature is maintained, watering is turned on at the right time, and all this taking into account the need for energy saving.
By the way, in 2008, the US National Intelligence Council put the Internet of Things on the list of six potentially damaging technologies. The report noted that the imperceptible ubiquity of Internet sites, which become such simple things as commodity packaging or paper documents, can cause damage to national information security.
And by 2010, the “Internet of things” has already become the driving force behind the idea of “foggy computing”, which extends the principle of cloud computing to a huge number of interacting geographically distributed devices, and turns into a platform of the “Internet of things”.
The technical side of the “Internet of things”
Even if a thing does not have a built-in means of communication, it may have an identifier on it. A barcode, QR code, or Data Matrix code can serve as an identifier. And for things connected to networks, the identifier, in particular, is the MAC address of the adapter, with which the device is identified at the channel level, but this is not very convenient due to the limited number of available addresses.
IPv6 provides a greater opportunity for identification, which gives a unique network layer address, and there can be more than 300 million such addresses on the planet for each earthling.
To convert information about the external environment into machine-friendly code, various measuring instruments are used, which play an important role for the Internet of things, filling the computing environment with priority information.
Among these tools are various sensors (light, temperature, humidity), metering devices (smart meters), and other systems, including complex integrated measuring systems. Measuring tools are combined in a network, for example, in a network of wireless sensors, from which entire systems of interaction between machines are built.
Measuring instruments should be as autonomous as possible, and first of all it concerns sensors, their energy saving. Ways to solve the problem are the use of alternative power sources, such as photocells, vibration energy converters, wireless power supply, etc. This is necessary in order to get rid of the constant need to recharge sensor batteries, replace batteries, etc., in general, for lower maintenance costs.
Data transfer technology for the Internet of things, in principle, includes all of today's wireless protocols. But it is extremely important that the selected technology meets the condition of efficiency at low speeds, is adaptive and fault tolerant, so that it can organize itself.
Most interesting from this point of view, IEEE 802.15.4, which defines the physical layer and controls access to provide energy-efficient personal networks, is the basis for the protocols: 6LoWPAN, ZigBee, MiWi, LPWAN, WirelessHart.
As for the wired methods, in the first place the PLC is the data transmission network over the wires of power lines, because many devices have a connection to the electric network, and what about smart meters, vending machines, lighting power supplies, ATMs - they always get power from the mains .
Particularly promising for the IoT is the open 6LoWPAN protocol, standardized by the IETF, which implements IPv6 over the PLC and over IEEE 802.15.4.
Security issue of the “Internet of things”
With one voice, experts insist that the suppliers of devices and services of the “Internet of Things” violate the principle of end-to-end information security recommended for all information and communication technology products. They say that information security should be laid at the start of design, and then only maintained all the time.
But what in reality? HP's summer 2014 research aimed to identify problems. Attention was drawn to problems on both sides - on the developer side and on the user side.
At the beginning of the use of “things”, a person needs to change the factory password to a unique one, his own, because by default they flogged the same everywhere. But not everyone is in a hurry to change the password!
Meanwhile, not every device has built-in protection, and this is the way to penetrate the home network through a device that has turned into an open gateway for an Internet attacker.It is imperative for the consumer to immediately take care of installing external protection.
HP research has shown that 7 out of 10 devices do not encrypt wireless traffic! 6 out of 10 have an insecure web interface vulnerable to cross-site scripting. Most devices initially provide passwords that are not strong enough. And finally, 9 out of 10 devices without the knowledge of their owner collect personal data!
Thus, the HP study revealed about 25 diverse vulnerabilities in televisions, household scales, door locks, sockets, security systems, as well as in their cloud and mobile components. The conclusion is depressing: today there is no security on the Internet of things. Targeted attacks, for example, pose a potential threat when, through an Internet thing, an attacker gains access to the owner’s world and personal space.
See also at bgv.electricianexp.com
:
